 Highly Reliable Systems now offers hardware encryption on select backup NAS devices. High-Rely supports AES encryption on many of our highly-removable drive backup appliances, allowing media to be safely transported. This article will discuss the encryption feature as supported on certain Netswap Plus and RAIDFrame Plus product lines (Not the BNAS or WBA Windows Storage Server based Appliances which have an encryption not discussed here).
Highly Reliable Systems now offers hardware encryption on select backup NAS devices. High-Rely supports AES encryption on many of our highly-removable drive backup appliances, allowing media to be safely transported. This article will discuss the encryption feature as supported on certain Netswap Plus and RAIDFrame Plus product lines (Not the BNAS or WBA Windows Storage Server based Appliances which have an encryption not discussed here).
Encryption on capable NetSwap and RAIDFrame server backup devices is used to protect data at rest, as well as when replicating offsite. This article is specifically referencing encryption of the hard drives themselves. Whether or not the backup software supports encryption, the NAS device and software can now protect data, which means many High-Rely backup devices now meet HIPAA and other regulatory compliance challenges.
The protection can be achieved by encrypting an entire disk or one individual file container, although we anticipate that the entire disk will be the usual option. The algorithm used is symmeteric key AES and the resulting volume is TrueCrypt compatible, which allows it to be mounted in a Windows or other machine with a free copy of TrueCrypt, or used as Amazon S3 compatible seed drives. TrueCrypt is an open-source disk encryption application. and is the only device encryption supported by Amazon Web Services for Import/Export. All seed drives returned by Amazon S3 to the customer will be encrypted in this way, so having this compatibility is crucial for High-Rely’s unique SpeedSeed feature.
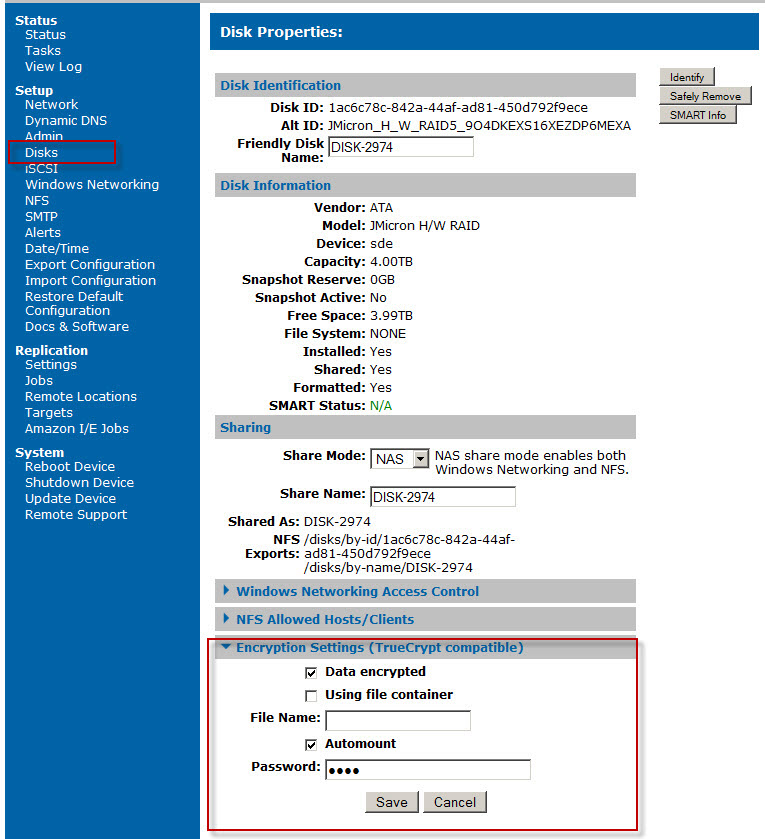
Encryption is configured under the “Disks” menu, typically when setting up and formatting your removable disks. The encryption engine supports parallelized encryption for multi-core systems to reduce the performance hit of encryption and decryption. On newer processors supporting the AES-NI instruction set, it supports hardware-accelerated AES to further improve performance, which is what is meant when we say High-Rely offers hardware support for encryption. TrueCrypt has at least one distinct advantage over Microsoft’s Bitlocker: Having support for multiple operating systems. Since the volumes are independent of the operating system, you will be able to mount your volume on any computer on which you can run TrueCrypt. These include:
- Windows 10 (32-bit and 64-bit)
- Windows 8/8.1 (32-bit and 64-bit)
- Windows 7 (32-bit and 64-bit)
- Windows Vista (32-bit and 64-bit)
- Windows XP (32-bit and 64-bit)
- Windows Server 2019 (64-bit)
- Windows Server 2016 (64-bit)
- Windows Server 2012/2012 R2 (64-bit)
- Windows Server 2008 R2 (64-bit)
- Windows Server 2008 (32-bit and 64-bit)
- Windows Server 2003 (32-bit and 64-bit)
- Windows 2000 SP4
Mac OS X 10.8 Mountain Lion (32-bit and 64-bit) - Mac OS X 10.7 Lion (32-bit and 64-bit)
- Mac OS X 10.6 Snow Leopard (32-bit)
- Mac OS X 10.5 Leopard
- Mac OS X 10.4 Tiger
Linux (32-bit and 64-bit versions, kernel 2.6 or compatible)
Note: The following operating systems (among others) are not supported: Windows RT, Windows 2003 IA-64, Windows 2008 IA-64, Windows XP IA-64, and the Embedded/Tablet versions of Windows.
Since TrueCrypt volumes do not contain file headers and their content is indistinguishable from random data, it is theoretically impossible to identify such drives as being TrueCrypt volumes without knowing their passwords. This is to support the concept of plausible deniability.
Note that the High-Rely implementation of encryption does not work if you use the drive in iSCSI mode. This is because the machine with the iSCSI initiator is in control of the low level format of the drive, bypassing the TrueCrypt engine. You can still use hardware encryption if the initiator has AES-NI by loading TrueCrypt on that side of the link (i.e. the server would become the encrypting machine rather than the backup appliance)
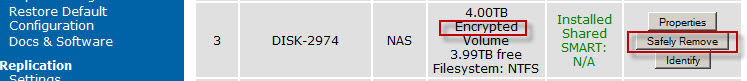
If a backup operation were active it is possible data loss may occur if you do an unsafe removal. We therefore recommend that before you unplug or turn off the Backup Appliance or remove a volume, you dismount the TrueCrypt volume first by doing clicking the safe remove button in the web interface of the appliance.
As can be seen in the nearby screenshot, the NAS setup allows the user to Automount encrypted volumes and enter a hidden password (the encryption key). This significantly increases the convenience of using encrypted volumes, as the password does not need to be entered each time the NAS is turned on. However, if the NAS is not stored in a locked room this option should be chosen with care as it means someone stealing the entire NAS could simply plug it in at an alternate location and gain access to the data. However, anyone stealing one of the removable drives would still require both the TrueCrypt engine and the encryption password, making transport of the removable drives a safe operation.
It is critical that the encryption password be remembered or securely recorded. We have not implemented any kind of ‘backdoor’ (and will never implement any ‘backdoor’ or deliberate weakness, even if asked to do so by a government agency), because it would defeat the purpose of the software. The source code for the engine is publicly available, independent researchers can verify that the source code does not contain any security flaw or secret ‘backdoor’. If the source code were not available, reviewers would need to reverse-engineer the executable files. However, analyzing and understanding such reverse-engineered code is so difficult that it is practically impossible to do (especially when the code is as large as the TrueCrypt code). There is no way to rescue encrypted data if the encryption key (password) is lost. We strongly suggest you save the key.
For a setup walkthru click here